CREST Approved Penetration Testing Services
Our CREST-accredited team tailor penetration tests to your unique technical environment, compliance needs and requirements, enabling you to understand your security vulnerabilities and take informed steps to mitigate risks.
CREST Approved Penetration Testing Services
Our CREST-accredited team tailor penetration tests to your unique technical environment, compliance needs and requirements, enabling you to understand your security vulnerabilities and take informed steps to mitigate risks.
Hacking Your Assets Legally
Penetration testing is a practice where ethical hackers attack an organization’ systems, networks, and applications to find and exploit vulnerabilities. The goal is to identify security weaknesses before malicious actors do, providing your organisation with actionable insights to strengthen your defences.
Experts in Penetration Testing
With 50+ CREST-registered consultants with over a decade of experience breaching banks, e-commerce giants, and insurance leaders – now using those same attack methods to secure your systems. We break into everything across your digital infrastructure (mobile, web, network, wireless), ensuring compliance with over 200 standards because getting hacked isn’t just expensive – it may be business-ending.
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Network
We secure your network infrastructure by identifying misconfigurations, weak protocols, and access control flaws across routers, switches, servers, and endpoints. We ensure compliance to many industry standards.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Achieve Compliance And Shield Your Assets
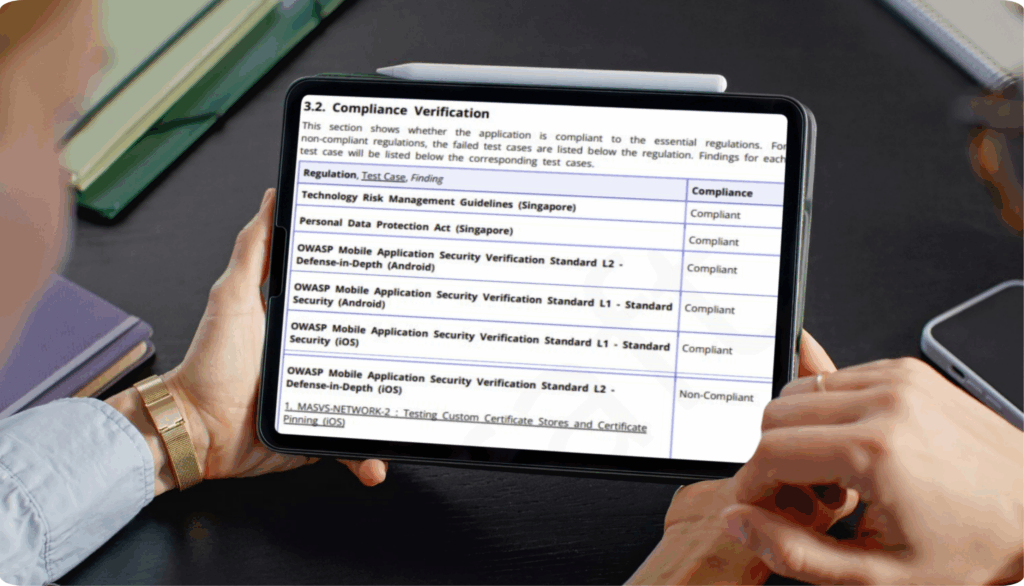
200+ Compliance Standards Covered
Velocity – our proprietary service delivery platform contains 20,000+ security checks mapped to 71 industry standards. From broad security standards like OWASP MASVS to market or industry-specific requirements like PCI-DSS for credit card security, we guarantee you’ll meet every relevant regulatory standard with precision and confidence.

Quality Across Every Engagement
Historically, penetration testing results can be inconsistent, relying heavily on the individual tester. Our structured testing framework on Velocity eliminates the lottery of individual tester skill – you get enterprise-grade results regardless of who’s on your project.
Reports That Deliver Value
We deliver comprehensive vulnerability reports at the end of the penetration test with detailed backgrounds, strategic recommendations, and clear impact statements. Each report is tailored for both technical teams and C-suite executives to ensure maximum value – because effective cybersecurity starts with reports that drive action.


Manage Your Asset’s Security At A Glance
Achieve Compliance And Shield Your Assets

200+ Compliance Standards Covered
Velocity – our proprietary service delivery platform contains 20,000+ security checks mapped to 71 industry standards. From broad security standards like OWASP MASVS to market or industry-specific requirements like PCI-DSS for credit card security, we guarantee you’ll meet every relevant regulatory standard with precision and confidence.

Quality Across Every Engagement
Historically, penetration testing results can be inconsistent, relying heavily on the individual tester. Our structured testing framework on Velocity eliminates the lottery of individual tester skill – you get enterprise-grade results regardless of who’s on your project.

Reports That Deliver Value
We deliver comprehensive vulnerability reports at the end of the penetration test with detailed backgrounds, strategic recommendations, and clear impact statements. Each report is tailored for both technical teams and C-suite executives to ensure maximum value – because effective cybersecurity starts with reports that drive action.

Manage Your Asset’s Security At A Glance

